As a Python developer, have you ever worried about the security of your code? With the increasing popularity of Python, it has become crucial to protect your code from unauthorized access and theft. Luckily, there are numerous free online obfuscation tools available that can help secure your Python code.
Python is widely used for its simplicity and readability, but this also means that your code can be easily understood and replicated by others. This poses a significant risk, especially if you are working on sensitive projects or commercial applications. To ensure the confidentiality and integrity of your code, it’s essential to take steps to obfuscate it.
In this comprehensive guide, we will explore the world of free online obfuscation tools for Python. We will discuss what obfuscation is and why it is necessary for securing your code. Additionally, we will provide an overview of the best free online obfuscation tools available, highlighting their features and benefits. By the end of this guide, you will have a clear understanding of how to protect your Python code effectively.
What is Python?
Python is a high-level programming language that is known for its simplicity, readability, and versatility. It was created by Guido van Rossum and first released in 1991. Python is widely used in various industries, including web development, data analysis, artificial intelligence, and even game development. It has a large and active community of developers who contribute to its extensive library of modules and packages. Python’s syntax is designed to be easy to understand and write, making it an excellent choice for both beginners and experienced programmers.
Additionally, Python’s interpreted nature allows for quick and easy prototyping, as well as efficient code execution. Its popularity and robustness have made Python one of the most widely used programming languages in the world.

Why is Python a Popular Choice for Software Development?
Python has emerged as one of the most popular programming languages for software development, and for good reason. Its simplicity and readability have made it an attractive option for developers of all levels of expertise.
One of the key reasons behind Python’s popularity is its ease of use. The language’s straightforward syntax and minimalistic approach make it accessible to beginners, while its powerful features and flexibility appeal to seasoned professionals. This ease of use not only reduces the learning curve but also speeds up development time, allowing programmers to focus on solving problems rather than dealing with complex code.
Python’s vast ecosystem of libraries and frameworks is another factor contributing to its popularity. The language offers a wide range of pre-built libraries for tasks such as data manipulation, web development, scientific computing, machine learning, and more. These libraries enable developers to leverage existing code and avoid reinventing the wheel, thereby improving productivity and accelerating application development.
Furthermore, Python’s simplicity and readability make it easier for developers to collaborate on projects. The clean and concise syntax promotes code readability, making it easier to understand, maintain, and debug. This clarity of code also facilitates teamwork, as developers can more easily share and contribute to each other’s work.
What is Code Obfuscation?
Code obfuscation is the practice of modifying executable code to make it unintelligible and difficult to reverse engineer, while maintaining its functionality. It involves transforming the code into a form that is often harder to understand and decipher, thus preventing unauthorized access to the original source code.
The primary purpose of code obfuscation is to protect intellectual property and secure Python code from unauthorized access. By making the code more complex and obscure, obfuscation prevents potential malicious actors from easily understanding and modifying the code. This helps safeguard valuable algorithms, proprietary methods, and other sensitive information embedded in the code.
Code obfuscation can be beneficial in various scenarios. For instance, when distributing commercial software developed in Python, obfuscation can prevent competitors from easily stealing or copying the code, protecting the company’s investment in development. Additionally, obfuscation can be useful when dealing with open-source projects, where securing the code against potential vulnerabilities or supply chain attacks is crucial.
Understanding the Need for Code Obfuscation
Code obfuscation plays a critical role in safeguarding intellectual property and securing Python code against unauthorized access. By making the code more complex and obscure, obfuscation prevents potential malicious actors from easily understanding and modifying the code. This is particularly important when distributing commercial software developed in Python, as obfuscation helps protect the company’s investment in development by making it difficult for competitors to steal or copy the code.
Similarly, obfuscation is valuable when working with open-source projects, where securing the code against potential vulnerabilities or supply chain attacks is of utmost importance. By obfuscating the code, developers can create an additional layer of protection, ensuring that sensitive information, valuable algorithms, and proprietary methods remain inaccessible to unauthorized individuals. Whether it is to protect intellectual property, prevent code theft, or enhance the security of open-source projects, code obfuscation serves as a crucial tool in securing Python code and preserving the integrity of software.
Benefits of Code Obfuscation
Code obfuscation offers several benefits in the field of software development, primarily enhancing security measures. By obfuscating code, developers can make it significantly harder for attackers to analyze and tamper with the code. This protection is particularly crucial for sensitive information and intellectual property. Obfuscation disguises the code’s structure, making it difficult for malicious actors to understand its functionality and exploit potential security vulnerabilities.
Additionally, code obfuscation can result in improved code performance by optimizing the code. Unnecessary metadata and duplicate codes can be stripped away, reducing the overall size of the codebase. This optimization leads to faster execution times and more efficient resource utilization.
Iterative code obfuscation is another technique that enhances security measures. By applying obfuscation techniques repeatedly, developers can create a complex and convoluted code structure. This confuses attackers and makes deobfuscation attempts significantly more challenging. The iterative nature of code obfuscation ensures a continuous layer of protection against potential security threats.
Overall, code obfuscation not only provides an added layer of security but also improves code performance. By making it harder for attackers to analyze and tamper with the code, sensitive information remains protected, and potential security vulnerabilities are mitigated. Furthermore, code optimization through obfuscation techniques results in faster execution times, enhancing the overall performance of the software.
Types of Threats to Python Code Security
1. Supply Chain Attacks: Malicious actors may compromise the integrity of open-source packages or package updates, leading to potential vulnerabilities in Python code. Developers should carefully evaluate the security configuration of the packages they incorporate into their codebase.
2. Brute Force Attacks: Attackers may attempt to gain unauthorized access to source code by systematically trying various combinations of input. Developers should ensure strong access controls and implement mechanisms to detect and prevent brute force attacks.
3. Code Modification: Unauthorized modification of code can introduce security vulnerabilities or malware into Python scripts. It is crucial for developers to regularly review code for any unexpected or suspicious changes.
4. Code Quality Issues: Poorly written code or insecure coding practices can lead to potential security vulnerabilities. Developers should adhere to secure coding guidelines, conduct secure code reviews, and use code checker tools to identify code quality issues.
5. Intellectual Property Theft: Python code may contain valuable intellectual property. Developers should protect their original code through techniques like obfuscation or legal measures to prevent unauthorized use or theft.
6. Access Control Issues: Improperly configured access controls can allow unauthorized individuals to gain access to sensitive code and intellectual property. Developers should implement robust access control mechanisms and regularly review and update access permissions.
7. Vulnerabilities in Open-Source Projects: Using open-source packages in Python code exposes developers to potential vulnerabilities if the projects they rely on have security flaws. Regularly monitoring and updating dependencies can help mitigate this risk.
8. Insider Threats: Employees or individuals with access to the codebase may intentionally or unintentionally compromise the security of Python code. Developers should have measures in place to detect and respond to potential insider threats.
Potential Vulnerabilities in Python Code
Python code, like any other code, is vulnerable to various security challenges that can compromise its integrity and expose it to potential vulnerabilities. Understanding these vulnerabilities is crucial for developers to take appropriate measures to secure their code.
One common security challenge is the use of easily guessable or insecure variable and function names. Poorly chosen names can make it easier for attackers to understand the code’s logic and potentially exploit it. To mitigate this risk, developers should use more meaningful and obfuscated names that hide the code’s purpose and intentions.
Another vulnerability in Python code is the risk of reverse engineering. Attackers can attempt to disassemble the code and analyze its structure, potentially identifying potential security weaknesses. Developers can protect against reverse engineering by using obfuscation techniques that make the code more difficult to understand and reverse engineer.
Intellectual property theft is another concern for Python code. Developers need to safeguard their original code from unauthorized use or theft. Obfuscation is one technique that can obscure the code’s logic and make it harder to duplicate or steal.
Lastly, even after obfuscation, syntax errors or other code quality issues can still be present. These issues can inadvertently expose potential vulnerabilities in the code. Developers must conduct thorough testing and secure code reviews to ensure that obfuscated code remains free from any syntax errors or other quality issues.
By addressing these potential vulnerabilities through practices like obfuscation, secure coding techniques, and code reviews, developers can enhance the security of their Python code and reduce the risk of exploitation.
Common Security Challenges with Python Code
Python code is vulnerable to various security challenges that developers need to be aware of in order to protect their code. One common challenge is the use of easily guessable or insecure variable and function names. By choosing poorly chosen names, developers make it easier for attackers to understand the code’s logic and potentially exploit it. To mitigate this risk, developers should use more meaningful and obfuscated names that hide the code’s purpose and intentions.
Another security challenge is the risk of reverse engineering, where attackers attempt to disassemble the code and analyze its structure. This can potentially reveal security weaknesses in the code. To protect against reverse engineering, developers can use obfuscation techniques that make the code more difficult to understand and reverse engineer.
Data anonymization techniques in Python also pose security risks and tradeoffs. While anonymization methods can help protect sensitive data, there is a risk of re-identification or data linkage, where malicious actors can use additional data sources to identify individuals. Developers need to carefully consider the techniques used and the potential impact on data security.
Furthermore, as Python heavily relies on open-source packages and projects, developers must navigate the evolving landscape of open-source security. They should keep up with package updates and security configurations to avoid potential vulnerabilities. Regular audits, secure code reviews, and adhering to security best practices are essential to ensuring the security of Python code in the face of evolving threats.
Free Online Tools and Resources for Obfuscating Your Python Scripts
Securing Python code is essential to protect intellectual property and prevent potential security vulnerabilities. As reverse engineering poses a risk to code integrity, obfuscation techniques can be used to make the code more challenging to understand and reverse engineer.
Overview of Free Online Obfuscation Tools Available For Python Scripts
1. Pyarmor: Pyarmor is an open-source online obfuscation tool specifically designed for Python scripts. It provides multiple levels of obfuscation, including renaming variables and functions, encrypting code objects, and inserting junk code. Pyarmor also offers features like access control, binding Python script to a specific machine, and checking the integrity of the obfuscated script. It is easy to integrate into existing projects and offers a command-line interface for automation.
2. Pyminifier: Pyminifier focuses on reducing the size of Python scripts by removing whitespace, comments, and docstrings. While it may not provide advanced obfuscation techniques, Pyminifier can be useful for reducing the visibility of the original code. It also offers options to obfuscate variable and function names, although this feature is not as comprehensive as dedicated obfuscation tools.
3. Pyobfuscate: Pyobfuscate is a web-based Python obfuscation tool that renames variables and functions, encrypts literal strings, and adds random junk code. It provides a user-friendly interface with options to customize the obfuscation level and generate obfuscated Python scripts. While Pyobfuscate may not offer the same level of complexity as other tools, it can be effective for basic obfuscation needs.
4. Pyminifierjs: Pyminifierjs is an online tool that combines JavaScript and Python obfuscation techniques. It minifies the Python code, removes comments and whitespace, and replaces variable and function names with shorter equivalents. The output is a JavaScript function that executes the obfuscated Python script. This tool can be useful for situations where running JavaScript is preferred over Python.
5. Pyprotect: Pyprotect is an online obfuscation tool that can be used to protect Python scripts from reverse engineering. It offers features such as renaming variables and functions, encrypting string literals, and injecting junk code. Pyprotect also provides an option to generate standalone executables that don’t require a Python interpreter. It is user-friendly, making it suitable for developers with little obfuscation experience.
Step-by-Step Guide to Obfuscating Your Python Code Using Python Obfuscator
A Python Obfuscator is a useful tool for securing your Python code by making it difficult to understand and reverse-engineer. Obfuscation is the process of transforming code into a form that is harder to read and comprehend, without altering its functionality. Here is a step-by-step guide to obfuscating your Python code using a Python Obfuscator:
1. Choose a Python Obfuscator tool: There are several free online Python Obfuscator tools available. Select one that suits your needs and download or access it.
2. Install the Python Obfuscator: Follow the instructions provided by the tool to install it on your system.
3. Select the Python script to obfuscate: Choose the Python script that you want to obfuscate and open it in the Python Obfuscator tool.
4. Rename internal identifiers: The obfuscation process involves renaming variables, functions, and classes in your code. This helps to hide the original intent and makes it harder for someone to understand your code.
5. Alter comments and docstrings: Comments and docstrings often provide hints about the code’s functionality. Modify or remove them to further obfuscate your code.
6. Encrypt code objects: The Python Obfuscator tool should have the capability to encrypt your code objects. Encrypting the code objects makes it even more challenging for malicious actors to understand your code.
By following these steps, you can increase the labor required to reverse-engineer your code. Remember to thoroughly test your obfuscated code to ensure that it still functions as intended. Obfuscation is not foolproof, but it adds an extra layer of complexity and deters casual attempts at code analysis.
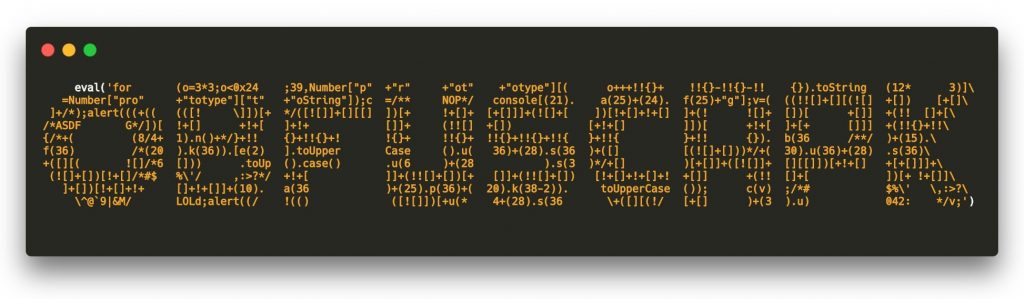
Best Practices for Effective Code Obfuscation
When it comes to code obfuscation, there are several best practices that can help ensure the security and effectiveness of your obfuscated code. Here are some key techniques and considerations to keep in mind:
1. Algorithm Selection: Choose obfuscation techniques that offer a high level of complexity and sophistication, making it difficult for potential attackers to reverse engineer your code. Some common techniques include encryption, junk code insertion, and string manipulation.
2. Layered Obfuscation: Implement multiple layers of obfuscation to make it even more challenging for attackers to understand your code. This can involve using a combination of different obfuscation techniques and applying them in a sequential manner.
3. Control Flow Obfuscation: Alter the control flow of your code by rearranging the order of statements or introducing redundant or irrelevant code blocks. This can make it significantly harder for attackers to follow the execution flow and understand the logic of your code.
4. Variable and Function Name Obfuscation: Rename variables and functions to more ambiguous or cryptic names, making it difficult to discern their purpose or meaning. This can help hide the original intent and functionality of your code.
5. Code Readability: While obfuscation aims to make code difficult to understand, it is important to strike a balance between obfuscation and readability. Maintain comments or documentation to aid in understanding the code during maintenance or by other developers who are authorized to access it.
6. Secure Integration: When integrating code obfuscation into your security toolkit, consider how the obfuscated code will be executed and stored. Ensure that proper security measures are in place to protect the obfuscated code from unauthorized access, and regularly update the obfuscation techniques to stay ahead of potential attackers.
By following these best practices, you can effectively obfuscate your code, enhancing its security and protecting your intellectual property.
Tips for Maintaining Readability While Obfuscating
When obfuscating your code to protect it from potential attackers, it is essential to strike a balance between code protection and maintainability. While the primary goal is to make the code difficult to understand, it is crucial to ensure that authorized developers can still comprehend and maintain the obfuscated code. Here are some tips for maintaining readability while obfuscating:
1. Variable Shuffling: One effective technique to obfuscate the behavior of variables and data storage is variable shuffling. Instead of using meaningful variable names, you can randomize or shuffle the names to obscure their purpose. This adds an extra layer of complexity for potential attackers while allowing authorized developers to understand the logic behind the obfuscated code.
2. Commenting and Documentation: Despite obfuscation, it is vital to include comments or documentation alongside the obfuscated code. This documentation can provide insights into the purpose, functionality, and specific requirements of the code. By maintaining informative comments, you enable authorized developers to understand the code during maintenance or debugging processes, ensuring the longevity of the codebase.
3. Code Structure: Maintaining a well-structured code is crucial for readability. Even though obfuscation techniques may introduce redundant or irrelevant code blocks, it is essential to structure the code in a logical and organized manner. This will help authorized developers navigate through the obfuscated code more easily.
4. Strike a Balance: When obfuscating your code, strike a balance between code protection and readability. Over-obfuscation can make the code overly complex and convoluted, negatively impacting maintainability. Therefore, carefully choose which parts of the code need maximum protection and which ones can remain more readable.
When evaluating the quality of an obfuscation technique, consider factors like the effectiveness of variable shuffling in obfuscating data storage, the level of difficulty for potential attackers, and the impact on code performance. By incorporating these considerations and techniques, you can maintain a balance between code protection and readability while obfuscating your code.
Integrating Code Obfuscation Into Your Security Toolkit
Integrating code obfuscation into a security toolkit provides numerous benefits and enhances the overall security of a Python codebase. Code obfuscation is the process of transforming code into an equivalent but more difficult-to-understand version, making it challenging for potential attackers to analyze and reverse-engineer the code. By incorporating code obfuscation techniques into a security toolkit, developers can effectively strengthen the protection of their Python code against unauthorized access and intellectual property theft.
Code obfuscation enhances security by making it significantly more challenging for malicious actors to understand the code’s functionality and logic. It obscures important details such as variable names, function names, and code structures, making it difficult for attackers to exploit potential security vulnerabilities. Additionally, obfuscated scripts are less likely to be susceptible to supply chain attacks, where attackers modify code during the distribution process to include malicious code.
There are various tools available for obfuscating Python scripts, including Obfuscapk, Pyminifier, and Pyarmor. These tools offer features such as variable renaming, control flow obfuscation, and constant folding to obfuscate the code effectively. It is important to note that while code obfuscation provides an additional layer of security, it is not a substitute for other security practices such as secure code review, dynamic analysis, and access control.
By integrating code obfuscation into a security toolkit, developers can fortify their Python codebase against potential vulnerabilities and unauthorized access to the source code. It is essential to strike a balance between code protection and maintainability to ensure that authorized developers can still comprehend and maintain the obfuscated code effectively.
Ensuring the Security of Your Python Codebase on Platforms like GitHub
Ensuring the security of your Python codebase on platforms like GitHub is crucial, especially when your code is publicly accessible. It is important to protect your code from potential threats and safeguard your intellectual property. Here are some best practices to follow:
1. Enable two-factor authentication (2FA): Implementing 2FA adds an extra layer of security by requiring a second form of authentication, like a temporary code or fingerprint, in addition to your password.
2. Restrict access to sensitive information: Avoid exposing sensitive information like API keys, passwords, or tokens in your codebase. Use environment variables or configuration files to store such information securely.
3. Regularly review and update code: Consistently review your codebase for potential vulnerabilities and apply security patches or updates promptly. Regularly updating dependencies and packages is crucial to avoid known security issues.
4. Utilize security tools: Take advantage of code analysis tools, static analysis tools, and code scanners that can help identify potential security vulnerabilities in your codebase. GitHub provides code scanning features that can automatically check for security issues.
5. Conduct code reviews: Engage your security team or peers in code reviews to identify and fix any potential security issues. Code reviews help catch vulnerabilities and ensure adherence to security best practices.
By implementing these measures, you can enhance the security of your Python codebase on platforms like GitHub. Protecting your code is essential to maintain the integrity and confidentiality of your intellectual property.
Conclusion
In conclusion, securing your Python code is of utmost importance to protect your intellectual property and reduce the risk of potential security vulnerabilities. Code obfuscation, such as utilizing a Python obfuscator, serves as an essential component of a comprehensive security strategy. By renaming variables and functions, obfuscation makes it harder for malicious actors to understand and modify your code, thus reducing the likelihood of a supply chain attack or unauthorized access to the source code. However, it is crucial to consider other security measures alongside obfuscation, such as encryption and data retention policies, to ensure the overall protection of your sensitive information.
Additionally, conducting secure code reviews, adopting access control protocols, and regularly updating and monitoring packages can help further identify and address potential vulnerabilities. Remember that while obfuscation can make your code more challenging to understand, it does not provide foolproof security and should be used in conjunction with other cybersecurity practices. By adhering to a comprehensive security strategy, including code obfuscation, you can enhance the integrity and confidentiality of your Python code base.